Secure Onboarding Devices With Secure Internet Access Gateway
– Identifies and secure endpoint devices with or without agents.

In today’s digital-first world, your internet is the lifeline of your business. But unmanaged access drains bandwidth, exposes you to threats, and drowns IT teams in compliance chaos. It’s time to turn your internet gateway into a competitive advantage.
Introducing Secure Internet Access Gateway
Internet Access Gateway isn’t just a firewall or a filter—it’s a unified platform that empowers IT to secure, optimize, and control internet usage across your entire organization. Whether you’re battling shadow IT, BYOD sprawl, or sophisticated cyberattacks, IAG delivers visibility, control, and peace of mind.
Why Internet Access Gateway (IAG) ?
Your Challenges:
- 🚨 Bandwidth bottlenecks from streaming, downloads, and unauthorized apps.
- 🚨 Cyberthreats like malware, phishing, and ransomware slipping through weak defenses.
- 🚨 BYOD chaos complicating security and compliance.
- 🚨 Productivity losses from social media, gaming, or illegal endpoints.
- 🚨 Regulatory risks due to poor visibility and reporting.
Our Solution:
✅ Bandwidth & User Access Management
To solve these common issuesIAG employs a URL & application database, which helps IT administrators effectively to enforce organization internet compliance by setting specific policies.AG also detects and blocks illegal Wi-Fi hotspots to avoid any information leakage from laptops, smartphones or tablets.
- Bandwidth Management: Guaranteed Bandwidth for Critical Applications
- User Access Management: Avoid Abuse by Restricting Access & Devices
- Application Control: Protect Enterprises Against Unauthorized Applications (6000+ Applications Eg Youtube, Facebook, TikTok, Rapidshare & etc.)
- URL Filtering: Monitor & Control Evasive Activities

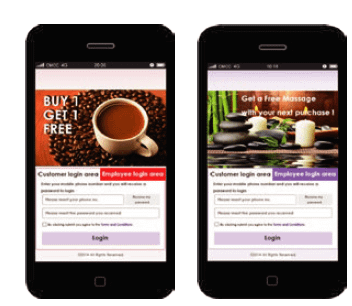
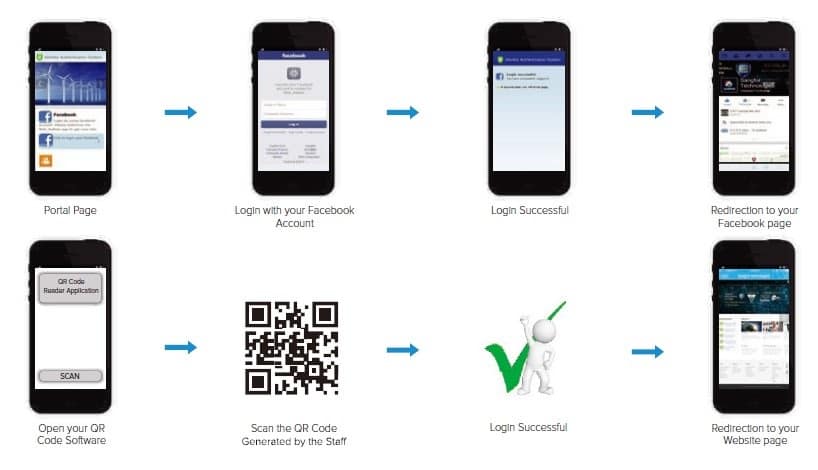
Authentication via QR Code
For companies receiving dozens of visitors per day, sharing the Wi-Fi password can become company risks. With IAG, you can create a QR code to allow your visitors to connect to the Wi-Fi simply by opening any QR code software and scan it. With this type of authentication, there is no need to change your Wi-Fi password every time and you can generate the QR Code according to each visitor group.
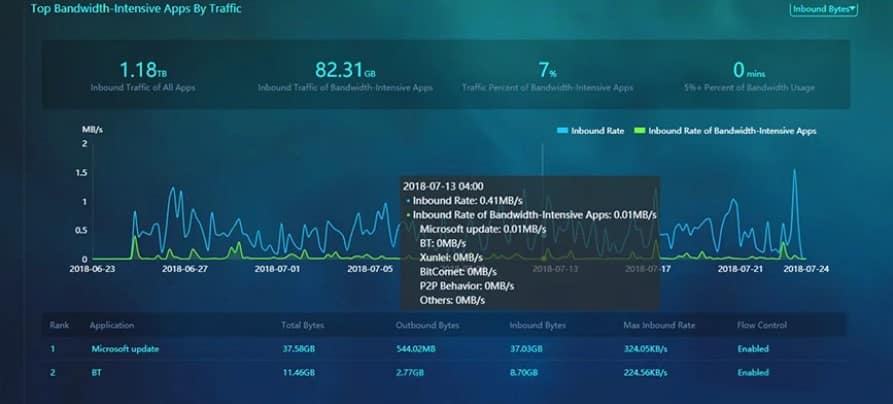
✅ Business Intelligence Platform
The newest significant development at IAG is the Business Intelligence Platform (BI). Based on IAG’s extensive internet log, it does a thorough modeling analysis of internet usage trends. It continuously applies behavioral awareness applications in various contexts and unearths useful information, assisting firms in comprehending behavior risk and streamlining O&M.
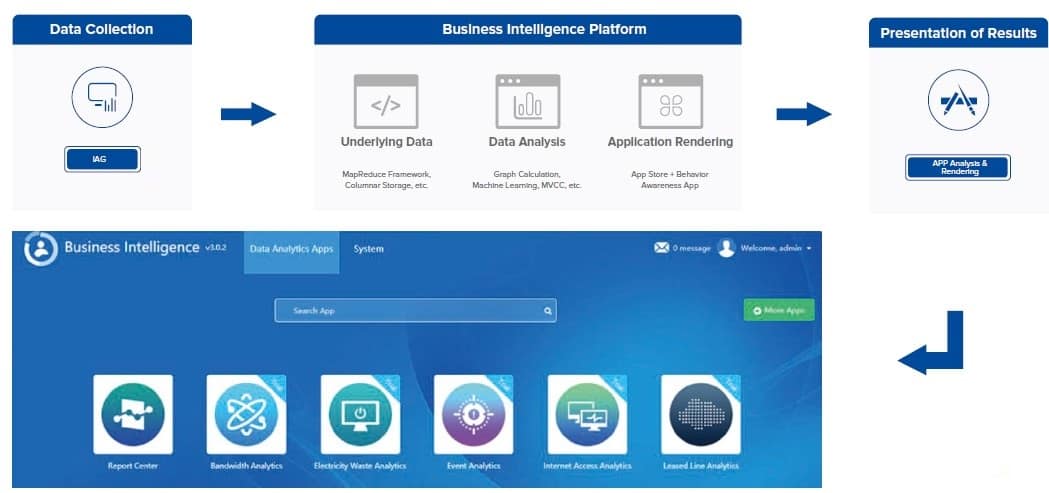
- Audit-Ready Reports: Generate GDPR, HIPAA, or PCI DSS compliance reports in seconds.
- Application Governance: Discover, group, and control risky apps (e.g., unapproved cloud storage) with built-in risk tagging.
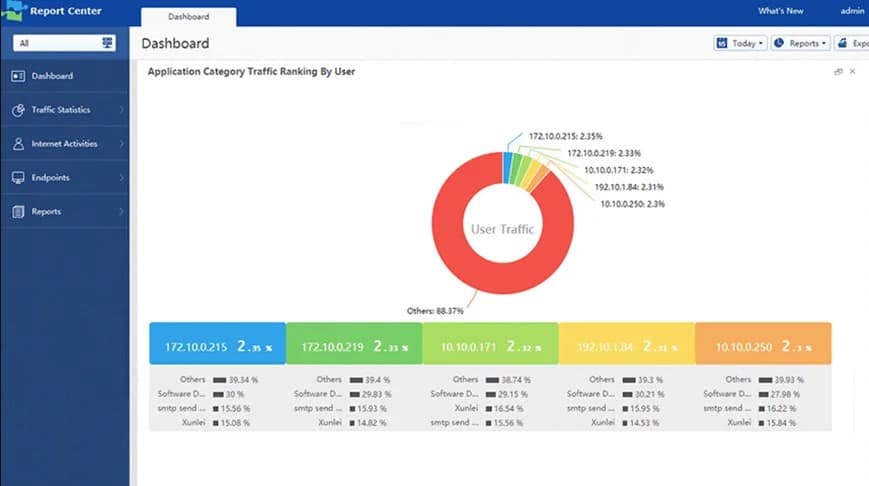
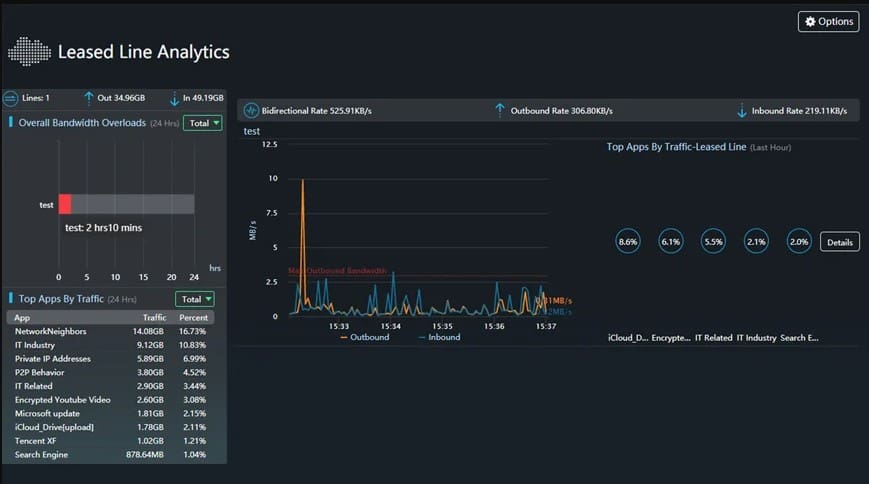
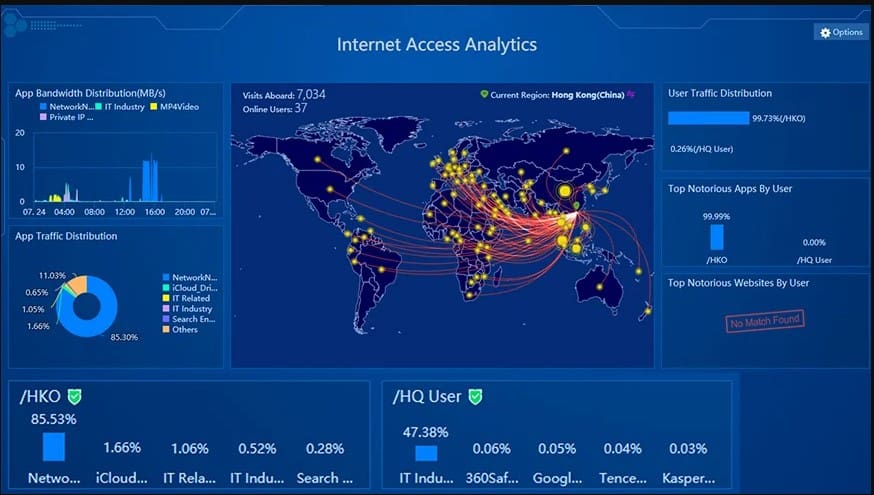
✅ 360° Visibility & Control
- BYOD Mastery: Automatically segment and secure mobile devices with granular policies.
- Endpoint Control: Management of Mobile Devices & Tablets
- Bandwidth Optimization: Prioritize critical apps (Zoom, SAP) and throttle Netflix/Torrents, cutting costs by 40%.
- SSL Decryption: Unmask hidden threats in encrypted traffic without performance loss.
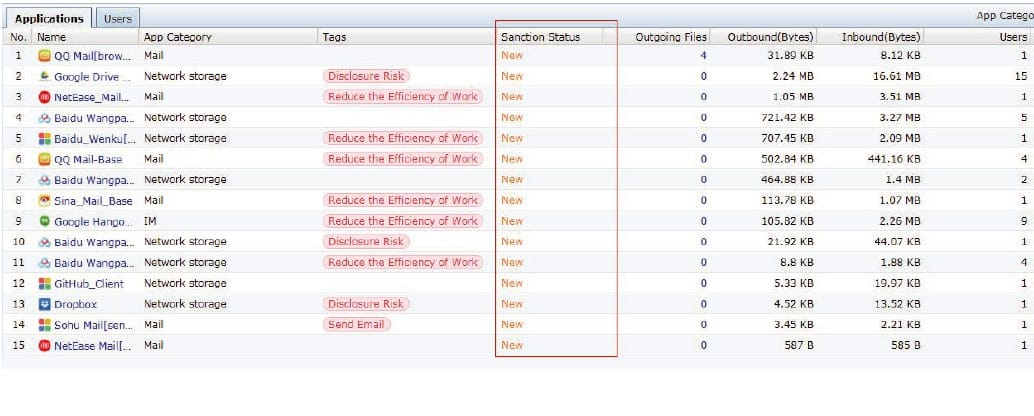
Discover Know the Risk
IAG’s built-in SaaS app database identifies top-used applications and groups them by risk (excessive emails, bandwidth drain, unproductive apps, data leaks). The dashboard displays real-time data usage and file transfers, giving IT admins clear visibility into network activity.
✅ Proactive Threat Defense
- AI-Driven DLP: Block data leaks via email, cloud storage, or USB with real-time monitoring.
- Proxy Avoidance Protection: Detect and block VPNs, anonymous browsers, and anti-proxy tools.
- Illegal Wi-Fi Detection: Stop rogue hotspots. Block Phishing Wi-Fi to Avoid Data Leakage
✅ Boost Productivity
- Safe Search Enforcement: Automatically filter inappropriate content on Google, Bing, and YouTube.
- Custom Playbooks: Automate responses to threats with pre-built or DIY SOAR workflows.
